Threat Watch
Transform your security from vulnerable to vigilant with an instant, comprehensive health scan.
Visit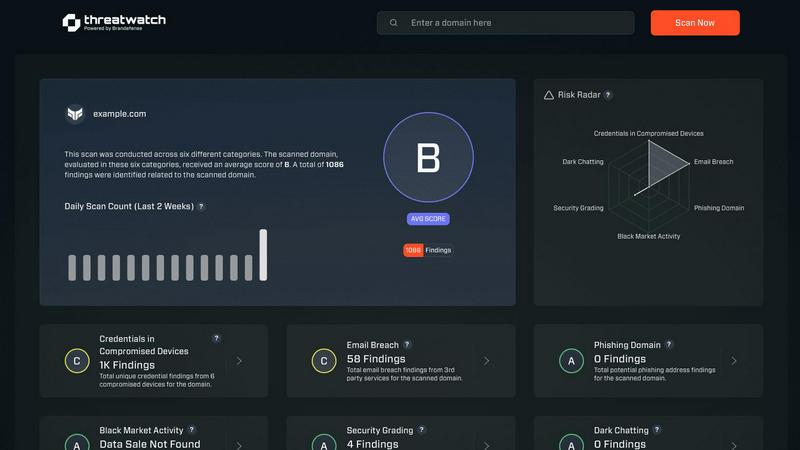
About Threat Watch
Threat Watch is your command center for cybersecurity confidence. It is a powerful, unified intelligence platform designed to transform how you understand and manage your organization's digital risk. In today's complex threat landscape, operating with fragmented information is a liability. Threat Watch eliminates the guesswork by continuously analyzing your entire digital footprint—from internal assets and software vulnerabilities to external exposures like compromised credentials and dark web mentions. It delivers a clear, actionable, and real-time picture of your cyber health, empowering you to move from a reactive security posture to a proactive, empowered stance. This solution is built for IT leaders, security teams, and business executives who demand clarity and control. Its core value proposition is speed and precision: by automating critical assessments and providing prioritized insights, Threat Watch enables you to identify, understand, and mitigate risks faster than ever before, turning cybersecurity from a constant challenge into a strategic advantage. Stop just defending and start leading with certainty.
Features of Threat Watch
Comprehensive Cyber Health Dashboard
Gain immediate, visual clarity into your organization's security posture with a unified dashboard. This central command center aggregates data across all critical categories, presenting your cyber health score, top risks, and trending threats in an intuitive, easy-to-understand format. Transform complex data into a clear narrative, empowering you to make informed decisions and communicate risk effectively to stakeholders without needing to be a deep technical expert.
Real-Time Exposure Monitoring
Go beyond traditional vulnerability scans with continuous, automated surveillance of your external digital presence. Threat Watch actively hunts for your organization's compromised credentials, breached accounts, phishing impersonations, and exposed data on the dark web. This real-time intelligence ensures you are the first to know about threats targeting your employees and assets, allowing you to act before attackers can exploit the information.
Automated Asset & Vulnerability Discovery
You cannot protect what you do not know exists. Threat Watch automatically discovers and catalogs your organization's internet-facing assets, software, and associated vulnerabilities. This continuous mapping eliminates blind spots and provides an always-current inventory, ensuring your security efforts are comprehensive and focused on your actual attack surface, not outdated assumptions.
Prioritized Risk Intelligence
Not all risks are created equal. Threat Watch cuts through the noise by applying context and intelligence to every finding. It analyzes vulnerabilities and exposures to assess their actual potential impact on your specific environment, delivering a prioritized list of actions. This means your team can focus their valuable time and resources on mitigating the most critical threats first, dramatically improving efficiency and effectiveness.
Use Cases of Threat Watch
Proactive Breach Prevention
Shift your strategy from cleaning up after attacks to preventing them entirely. By continuously monitoring for stolen employee credentials and corporate data on dark web markets, Threat Watch provides early warning signs of impending attacks. This allows your security team to force password resets, revoke access, and shore up defenses before criminals can use the leaked information to breach your network.
Streamlining Security Audits & Compliance
Prepare for audits with confidence and ease. Threat Watch provides continuous documentation of your security controls, asset inventory, and risk mitigation activities. Generate up-to-the-minute reports on your security posture for frameworks like ISO 27001 or SOC 2, demonstrating due diligence and a proactive approach to risk management to auditors and clients alike.
Third-Party & Supply Chain Risk Assessment
Extend your security vigilance to your partners and vendors. Use Threat Watch to assess the external cyber health of companies in your supply chain by monitoring for their public exposures and breaches. This intelligence helps you understand your indirect risk and initiate informed conversations with third parties about their security practices, protecting your ecosystem.
Executive & Board-Level Risk Reporting
Communicate cybersecurity in business terms. The clear, dashboard-driven insights from Threat Watch translate technical vulnerabilities into business risk narratives. Security leaders can use these reports to provide the executive team and board with a concise, compelling view of the organization's cyber health, justifying investments and aligning security strategy with business objectives.
Frequently Asked Questions
How does the free scan work?
The free scan is a powerful starting point for your cybersecurity transformation. By simply providing your organization's domain name, Threat Watch initiates a non-intrusive discovery process. It scans public sources and databases to identify associated assets, known vulnerabilities, and critically, uncovers if any employee credentials or company data have been exposed in known breaches or are circulating on the dark web. You receive a high-level report revealing key findings, giving you immediate insight into your external exposure without any commitment.
What makes Threat Watch different from a traditional vulnerability scanner?
Traditional scanners primarily look inward at your network for technical software flaws. Threat Watch provides a holistic, intelligence-led view. It combines internal asset and vulnerability discovery with external threat intelligence, monitoring the clear and dark web for active threats targeting your organization specifically. This combination of internal posture and external threat context is what creates a true picture of your "cyber health" and allows for truly prioritized risk action.
Is Threat Watch suitable for a small business without a dedicated IT team?
Absolutely. Threat Watch is designed to empower organizations of all sizes. For smaller teams, its automated discovery, clear dashboard, and prioritized alerts are invaluable. It acts as a force multiplier, doing the continuous monitoring work that a small team cannot manually perform. The actionable, plain-language insights allow business owners or general IT staff to understand and address critical risks effectively, making enterprise-grade cybersecurity accessible.
How often is my organization's threat data updated?
Threat Watch operates on a continuous, real-time intelligence model. Our systems are constantly ingesting data from a vast array of global sources, including threat feeds, breach databases, dark web forums, and public internet scans. Your dashboard and alerts are updated dynamically as new information about your assets, vulnerabilities, or exposed data is discovered, ensuring you always have the most current picture of your risk environment.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Zignt
Zignt empowers teams to sign contracts instantly and securely, transforming how you work.
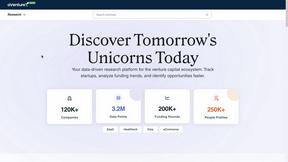
aVenture
Unlock institutional-grade venture intelligence to research any private company and seize emerging opportunities.