Binary Vulnerability Analysis
About Binary Vulnerability Analysis
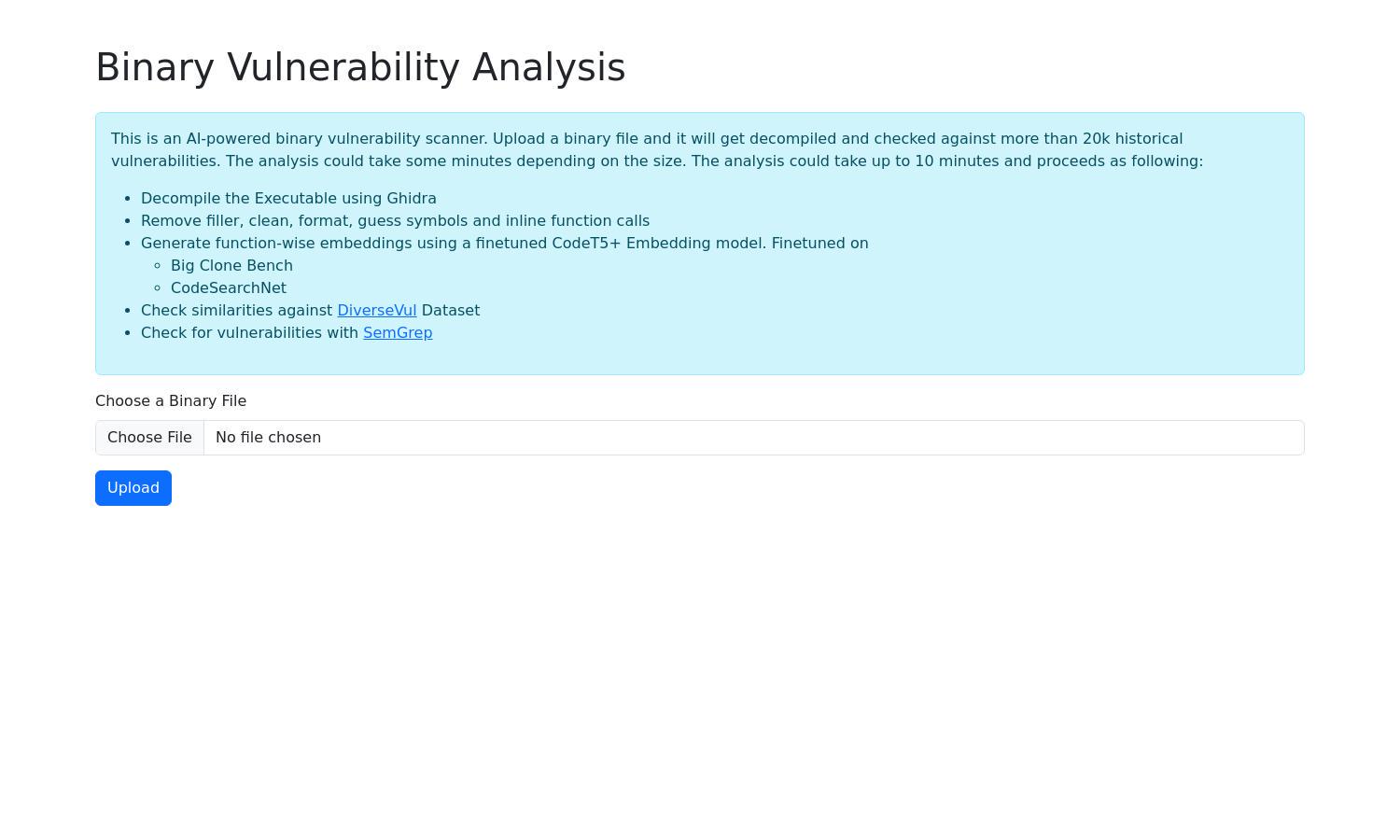
Binary Vulnerability Analysis offers a powerful AI-driven solution for assessing binary file security. Users upload their executable files, which are decompiled and analyzed for vulnerabilities based on historical data. This streamlined process saves time, enhances software safety, and safeguards against potential exploits.
Binary Vulnerability Analysis features tiered pricing plans that cater to different user needs. Each subscription provides access to advanced scanning features, with discounts available for longer commitments. Upgrading maximizes security benefits, enhancing users' ability to protect their binaries from potential threats.
The user interface of Binary Vulnerability Analysis is designed for ease and efficiency. Its layout promotes a seamless experience, allowing users to upload files and receive analysis results without hassle. Unique features like real-time vulnerability checking enhance usability and accessibility.
How Binary Vulnerability Analysis works
To use Binary Vulnerability Analysis, users start by registering and uploading their binary files. The platform decompiles the executables, removing unnecessary data, and formats the code for analysis. Advanced AI techniques then compare results against a comprehensive historical database, identifying potential vulnerabilities and providing users with valuable insights for securing their software.
Key Features for Binary Vulnerability Analysis
AI-Powered Vulnerability Scanning
Binary Vulnerability Analysis features an innovative AI-powered scanning system that quickly identifies vulnerabilities in uploaded binary files. This unique approach not only enhances security but also significantly reduces the time required for assessments, providing users with prompt and reliable vulnerability insights.
Comprehensive Database Access
A standout feature of Binary Vulnerability Analysis is its access to a comprehensive database of over 20,000 historical vulnerabilities. This extensive resource allows users to effectively benchmark their binaries against a wide array of known threats, ensuring thorough and accurate vulnerability assessments.
Real-Time Analysis
Binary Vulnerability Analysis provides real-time analysis of binary files, enabling users to receive immediate feedback about vulnerabilities. This instant feedback mechanism empowers users to make timely decisions regarding software security, enhancing their overall defensive strategies against potential threats.
You may also like: